- Joined
- Oct 12, 2023
- Messages
- 186
- Reaction score
- 35
In April-May 2024 alone, the Internet Corporation for Assigned Names and Numbers (ICANN) received 1,558 complaints about different types of abuse, including DNS abuse. However, many cases remain undetected, putting businesses of all sizes at risk of losses from cyberattacks.
The Domain Name System (DNS) is a crucial component of any website’s operation. It serves as the main traffic routing system, ensuring that websites load correctly and are accessible to users. Due to its importance, DNS has become a prime target for destructive cyberattacks.
If the DNS infrastructure is not functioning well, websites won’t load properly. Cybercriminals can redirect website traffic to malicious servers to steal data or install malware, using advanced techniques such as domain hijacking and cache poisoning to infiltrate DNS records and infrastructure.
According to the IDC’s 2022 Global DNS Threat Report, 88% of companies have experienced at least one DNS attack, with an average cost of about $942,000. Typically, companies experience about seven attacks per year.
In its 2024 report, Interisle, which specializes in internet technology and network strategy, found that between September 2023 and August 2024, a total of 16.3 million attacks were recorded – 54% more than a year ago. Among these attacks, 8.6 million used unique domains, close to doubling last year’s number.
Even if your business has not been prone to DNS abuse in the past, it’s important to understand the threat and implement security measures to mitigate potential risks.
DNS (Domain Name System) is a system that translates human-readable domain names into Internet Protocol (IP) addresses, which computers use to identify each other on the network.
DNS abuse is a malicious activity aimed at disrupting the DNS infrastructure or causing it to operate unintendedly. Abusive activities include corrupting DNS zone data, gaining administrative control of a name server, and flooding the DNS with thousands of messages to degrade name-resolution services.
According to the Internet and Jurisdiction Policy Network*, ICANN recognizes five main categories of DNS abuse:
The wider range of DNS security threats includes:
*The Internet and Jurisdiction Policy Network is a multi-stakeholder organization that aims to address challenges arising between the global internet and national jurisdictions.
The Secretariat of this organization facilitates a global policy process involving over 400 key stakeholders from governments, the world’s largest internet companies, technical operators, civil society groups, academia, and international organizations in over 70 countries.
Understanding the potential risk is the first step – now let’s see what can be done to protect your company from DNS abuse.
1. Register a domain with security in mind. If you want to create a new domain, check the domain extension, or at least, read the reviews. Otherwise, you might come across an extension like .ICU, which is well-known for sending spam. By December 2019, there had been 6,799 reported attempts to deliver spam from .ICU domains. Subsequently, ICANN decided to conduct a purge of this domain extension, removing most of the domains. If you purchase a domain with a disreputable suffix, you may end up losing it or suffer damage to your image when using the extension.
When registering a pre-used domain, check its history. This includes what websites were previously hosted on the domain, what backlinks they had, and who owned the domain. The easiest way to do this is on the Wayback Machine or by using the Who.is service, which provides WHOIS data.
2. Monitor and analyze traffic regularly. Set up DNS monitoring systems to detect suspicious activity. Here are some tools to analyze traffic and identify unusual patterns that indicate an attack or abuse:
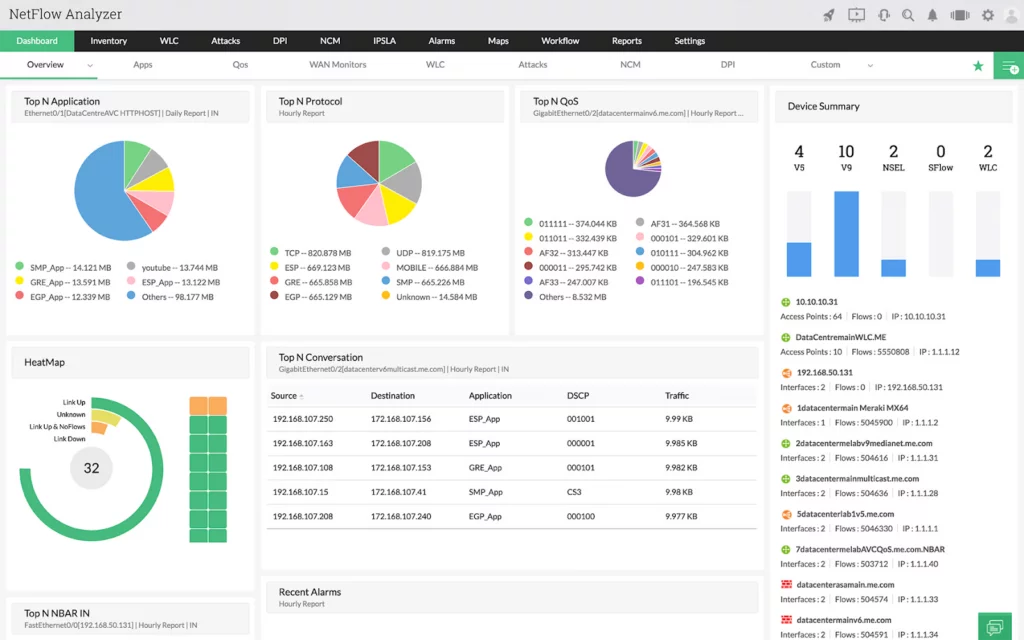
ManageEngine NetFlow Analyzer provides detailed traffic information so you can easily spot suspicious activity and take action in a timely manner.
Source: GEEKFLARE
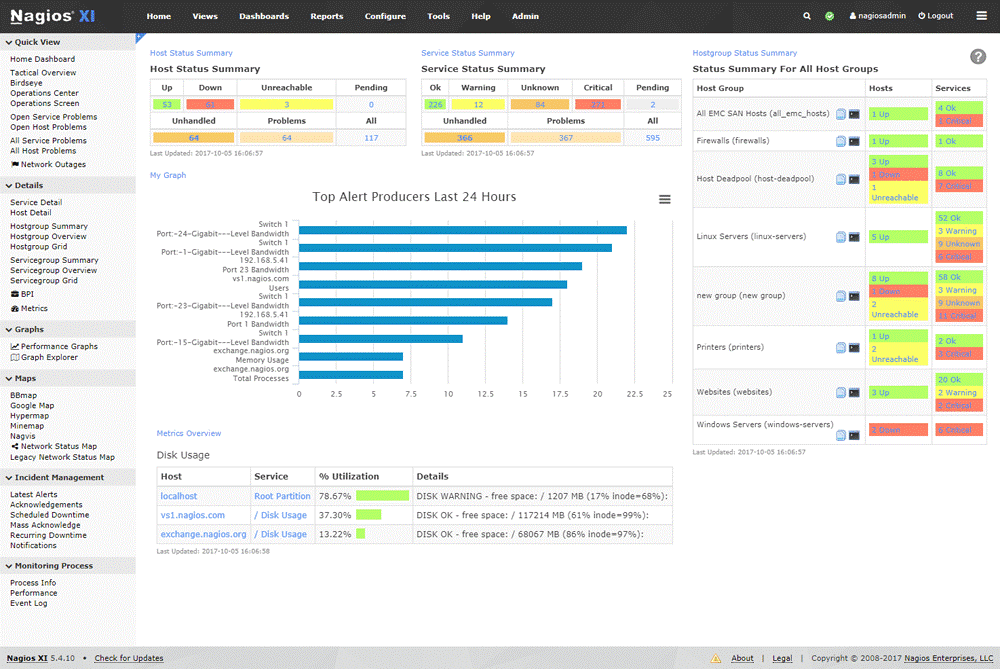
DNS Monitoring. Source: Atatus
This is one of the screens of the Statistics section.
3. Use DNSSEC. DNS Security Extensions (DNSSEC) is a set of tools that enhances the security of the DNS. By verifying the authenticity of responses to DNS queries, DNSSEC helps prevent attacks such as cache poisoning. It guarantees the integrity and trustworthiness of the data.
Enabling DNSSEC protection for a domain involves the following steps:
To enable and maintain DNSSEC, you need to manually publish and update DS records (Delegation Signer) in the parent domain zone.
DNSSEC operates on the principle of digital signatures. The administrator maintains records of domain names and corresponding IP addresses. For each record, DNSSEC assigns a unique digital signature that is closely matched to it. All responses from DNSSEC are backward compatible and include a digital signature.
4. Filter and block malicious domains. Use DNS filtering solutions to block access to known malicious websites by using blacklists, whitelists, category filtering, and custom policies. Some DNS filtering services include AdGuard DNS, Cisco Umbrella, and NextDNS.
Blocking malicious domains ensures protection against network threats such as ransomware and phishing, enables more control over content and compliance with industry regulations.
5. Incident Management and Response. Have a clear incident response plan for DNS abuse and plan for creating an incident management team – cybersecurity and data privacy experts, lawyers and business stakeholders – to analyze and mitigate the impact.
Typically, incident response starts when the security team receives a credible alert from a security information and event management (SIEM) system. The team should then determine whether the event qualifies as an incident and isolate the affected systems to mitigate the threat.
Sometimes incidents have consequences that take a long time to resolve. In such cases, companies may need to restore data from backups, deal with ransomware, or notify customers that their data has been compromised.
6. Regular updates and patches. Keeping your software and systems up to date helps protect them from known vulnerabilities that could be exploited for DNS abuse.
7. Follow domain name registrars. Keep a close eye on the notifications from your domain registrar. They can provide information about suspicious domains, or you can ask for their assistance in identifying, investigating, and resolving any issues related to security.
8. Follow Security Communities and Initiatives. Staying up-to-date on the latest trends and threats related to DNS abuse. Additionally, it allows organizations to share their experiences and best practices with other participants.
ICANN has established a DNS Abuse Mitigation Program. This program serves as a centralized platform for ICANN to address various aspects of DNS abuse and aims to support the ICANN community in mitigating harmful activities associated with domain names. ICANN has the following measures to combat DNS abuse:
DNS abuse is a serious threat to companies and users. However, with the help of the measures and tools mentioned above, you can reduce its likelihood and impact.
Looking for more tips to protect your business online? Visit it.com Domains blog and contact us on social media.
Continue reading on the it.com Domains blog...
The Domain Name System (DNS) is a crucial component of any website’s operation. It serves as the main traffic routing system, ensuring that websites load correctly and are accessible to users. Due to its importance, DNS has become a prime target for destructive cyberattacks.
If the DNS infrastructure is not functioning well, websites won’t load properly. Cybercriminals can redirect website traffic to malicious servers to steal data or install malware, using advanced techniques such as domain hijacking and cache poisoning to infiltrate DNS records and infrastructure.
According to the IDC’s 2022 Global DNS Threat Report, 88% of companies have experienced at least one DNS attack, with an average cost of about $942,000. Typically, companies experience about seven attacks per year.
In its 2024 report, Interisle, which specializes in internet technology and network strategy, found that between September 2023 and August 2024, a total of 16.3 million attacks were recorded – 54% more than a year ago. Among these attacks, 8.6 million used unique domains, close to doubling last year’s number.
Even if your business has not been prone to DNS abuse in the past, it’s important to understand the threat and implement security measures to mitigate potential risks.
What is DNS Abuse?
DNS (Domain Name System) is a system that translates human-readable domain names into Internet Protocol (IP) addresses, which computers use to identify each other on the network.
DNS abuse is a malicious activity aimed at disrupting the DNS infrastructure or causing it to operate unintendedly. Abusive activities include corrupting DNS zone data, gaining administrative control of a name server, and flooding the DNS with thousands of messages to degrade name-resolution services.
Types of DNS Abuse
According to the Internet and Jurisdiction Policy Network*, ICANN recognizes five main categories of DNS abuse:
- Botnets. A botnet is a network of devices infected with malware (bots) that follow commands from a central command and control (C&C) server. In this type of DNS abuse, domain names are used to identify hosts that control botnets and collections of malware-infected computers. These can be used to carry out various malicious activities, such as spam or phishing campaigns.
- Malware. Domain names that allow for the hosting and distribution of harmful or intrusive software, which may be installed on end-user systems without their knowledge or consent.
- Pharming. A type of fraud where someone pretends to be someone else’s website to steal information. The attacker changes the IP address of a well-known domain name. When users visit the site with the modified IP address, they are directed to the attacker’s website, which is disguised to look like the original domain owner’s site.
- Phishing. Attackers create fake websites that look like they are genuine. They do this to steal sensitive information such as usernames and passwords. They may use DNS to redirect users to these fake websites.
- Spam. It is used as a means to distribute the forms of DNS abuse mentioned above. These include domains that are advertised in unauthorized bulk email campaigns or used as names for spam email exchange systems.
The wider range of DNS security threats includes:
- Denial of Service (DoS) Attacks. DoS attacks are designed to make a website or server inaccessible by making it unresponsive. This can be achieved in several ways, for instance, by flooding the website with so much traffic that it can’t respond to queries anymore. Alternatively, the attacker may exploit security vulnerabilities in the system to make it unstable.
- Distributed Denial of Service (DDoS) Attacks. DDoS attacks aim to overwhelm websites or servers with traffic from multiple sources, making the site inaccessible.
- Cache Poisoning. The attacker sends fake DNS responses to queries. They make the server think the wrong data is correct for a particular domain. The server stores this incorrect answer in its cache and provides it when future lookups are performed.
- Protocol Attacks. It takes advantage of a specific feature or an implementation bug in a protocol installed on the victim’s computer to consume too many resources.
*The Internet and Jurisdiction Policy Network is a multi-stakeholder organization that aims to address challenges arising between the global internet and national jurisdictions.
The Secretariat of this organization facilitates a global policy process involving over 400 key stakeholders from governments, the world’s largest internet companies, technical operators, civil society groups, academia, and international organizations in over 70 countries.
How to Fight DNS Abuse
Understanding the potential risk is the first step – now let’s see what can be done to protect your company from DNS abuse.
1. Register a domain with security in mind. If you want to create a new domain, check the domain extension, or at least, read the reviews. Otherwise, you might come across an extension like .ICU, which is well-known for sending spam. By December 2019, there had been 6,799 reported attempts to deliver spam from .ICU domains. Subsequently, ICANN decided to conduct a purge of this domain extension, removing most of the domains. If you purchase a domain with a disreputable suffix, you may end up losing it or suffer damage to your image when using the extension.
When registering a pre-used domain, check its history. This includes what websites were previously hosted on the domain, what backlinks they had, and who owned the domain. The easiest way to do this is on the Wayback Machine or by using the Who.is service, which provides WHOIS data.
2. Monitor and analyze traffic regularly. Set up DNS monitoring systems to detect suspicious activity. Here are some tools to analyze traffic and identify unusual patterns that indicate an attack or abuse:
- ManageEngine NetFlow Analyzer collects and analyzes network traffic data. This tool provides real-time network traffic information and allows you to monitor, analyze, and manage network activity.

ManageEngine NetFlow Analyzer provides detailed traffic information so you can easily spot suspicious activity and take action in a timely manner.
Source: GEEKFLARE
- Nagios enables you to keep track of DNS traffic on your network. It generates detailed reports and presents the DNS monitoring data in a visual format, including graphs, charts, and dashboards.

DNS Monitoring. Source: Atatus
- Wireshark, a traffic analyzer that can detect malicious data flows. You need to record and open the DNS traffic filter between clients and your own DNS server. Then you save the data in a PCAP (Packet Capture) file and create scripts to search for suspicious activity patterns in the file.

This is one of the screens of the Statistics section.
3. Use DNSSEC. DNS Security Extensions (DNSSEC) is a set of tools that enhances the security of the DNS. By verifying the authenticity of responses to DNS queries, DNSSEC helps prevent attacks such as cache poisoning. It guarantees the integrity and trustworthiness of the data.
Enabling DNSSEC protection for a domain involves the following steps:
- Check the maximum TTL (Time to Live) value in the domain zone.
- Sign the domain zone.
- Create a chain of trust.
To enable and maintain DNSSEC, you need to manually publish and update DS records (Delegation Signer) in the parent domain zone.
DNSSEC operates on the principle of digital signatures. The administrator maintains records of domain names and corresponding IP addresses. For each record, DNSSEC assigns a unique digital signature that is closely matched to it. All responses from DNSSEC are backward compatible and include a digital signature.
4. Filter and block malicious domains. Use DNS filtering solutions to block access to known malicious websites by using blacklists, whitelists, category filtering, and custom policies. Some DNS filtering services include AdGuard DNS, Cisco Umbrella, and NextDNS.
Blocking malicious domains ensures protection against network threats such as ransomware and phishing, enables more control over content and compliance with industry regulations.
5. Incident Management and Response. Have a clear incident response plan for DNS abuse and plan for creating an incident management team – cybersecurity and data privacy experts, lawyers and business stakeholders – to analyze and mitigate the impact.
Typically, incident response starts when the security team receives a credible alert from a security information and event management (SIEM) system. The team should then determine whether the event qualifies as an incident and isolate the affected systems to mitigate the threat.
Sometimes incidents have consequences that take a long time to resolve. In such cases, companies may need to restore data from backups, deal with ransomware, or notify customers that their data has been compromised.
6. Regular updates and patches. Keeping your software and systems up to date helps protect them from known vulnerabilities that could be exploited for DNS abuse.
7. Follow domain name registrars. Keep a close eye on the notifications from your domain registrar. They can provide information about suspicious domains, or you can ask for their assistance in identifying, investigating, and resolving any issues related to security.
8. Follow Security Communities and Initiatives. Staying up-to-date on the latest trends and threats related to DNS abuse. Additionally, it allows organizations to share their experiences and best practices with other participants.
ICANN has established a DNS Abuse Mitigation Program. This program serves as a centralized platform for ICANN to address various aspects of DNS abuse and aims to support the ICANN community in mitigating harmful activities associated with domain names. ICANN has the following measures to combat DNS abuse:
- The Inferential Analysis of Maliciously Registered Domains (INFERMAL) project. Cybercriminals often register domains to do phishing, malware distribution, and spam campaigns. There are many reasons why these actors prefer certain registrants over others. The goal of INFERMAL is to systematically analyze the preferences of attackers.
- The Special Interest Forums on Technology (SIFT). This forum is used for technical discussions and review contributions on emerging technologies and trends related to the Internet’s identifier system. This includes domain names and the DNS, IP addresses, autonomous system numbers, and various protocol parameter assignments.
DNS abuse is a serious threat to companies and users. However, with the help of the measures and tools mentioned above, you can reduce its likelihood and impact.
Looking for more tips to protect your business online? Visit it.com Domains blog and contact us on social media.
Continue reading on the it.com Domains blog...



